Fuzzing with nuclei
LFI Example
LFI (Local File Inclusion) is a vulnerability that allows an attacker to read files on the server. In this example, we will use a template to detect LFI vulnerabilities.
- Download the Template
-
To get the example template run:
wget https://gitlab.com/brendan/fuzzbuzz/-/raw/main/examples/linux-lfi.yaml
or get the file here. - Run the command
-
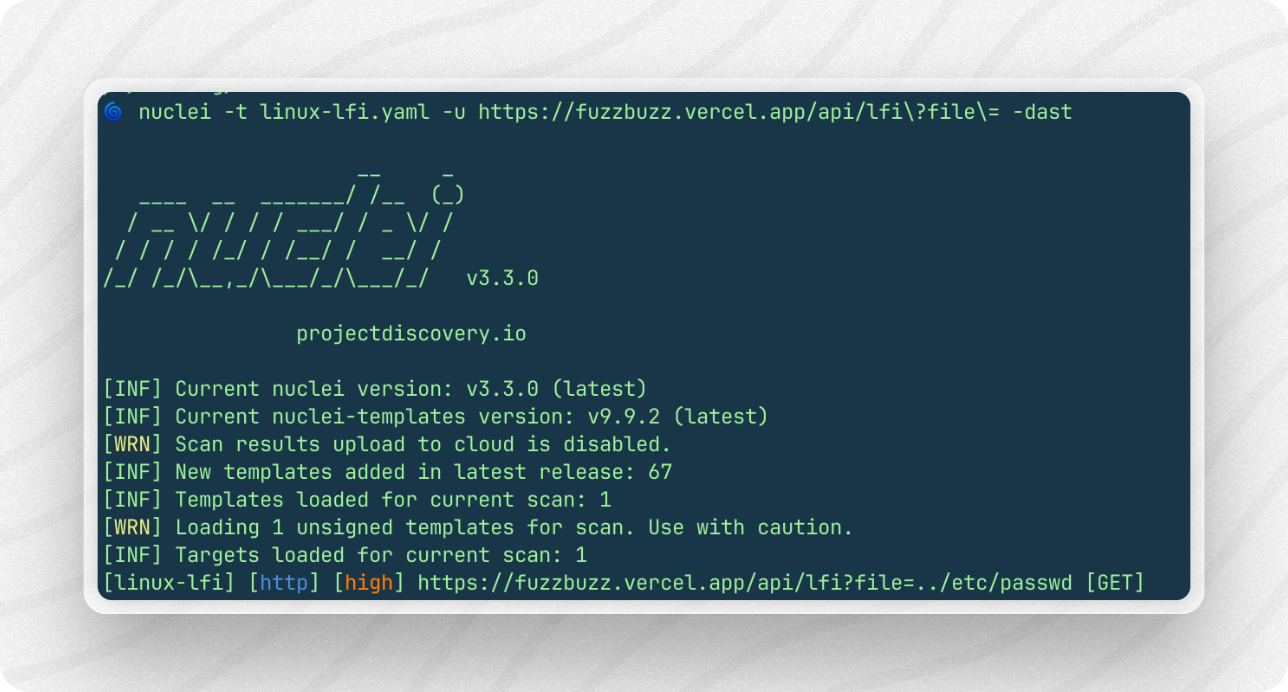
To run the template, in the same folder run this command:
nuclei -t linux-lfi.yaml -u https://fuzzbuzz.vercel.app/api/lfi\?file\= -dast - Explaining the command
-
The first part of the command uses
-tto tell nuclei to use the local template file `linux-lfi.yaml`:
nuclei -t linux-lfi.yaml
The second part of the command uses-uto specify the URL to test:
-u https://fuzzbuzz.vercel.app/api/lfi\?file\=
Note that it escalates the URL with the parameter `file=` to test for LFI.
The last part of the command uses-dastto enable the DAST engine to fuzz test for LFI vulnerabilities. - Expected output
-
The output of your command should look something like: